search the site
Maritime industry publishes updated guidelines for cyber security on ships

Maritime industry publishes updated guidelines for cyber security on ships
With cyber threats constantly evolving, cyber related processes on board ships need to successfully provide protection against cyber attacks. For this reason, BIMCO along with several maritime industry organisations published the third version of the ‘Guidelines on Cyber Security onboard Ships’.
Cyber Security | 10/12/18
Cyber safety incidents can occur as the result of:
- A cyber security incident, which affects the availability and integrity of OT, for example corruption of chart data held in an Electronic Chart Display and Information System (ECDIS);
- A failure happening during software maintenance and patching;
- Loss of or manipulation of external sensor data, critical for the operation of a ship. This includes but is not limited to Global Navigation Satellite Systems (GNSS).
To mitigate these dangers, the new guidelines are focusing on three new areas: Safety Management System, OT risks and supply chain dangers. Namely, they provide guidance to shipowners and operators on how to assess their operations and establish procedures to enhance cyber resilience on board their vessels.
Safety Management System
This new edition provides more information to assist shipping companies conduct proper risk assessments and include measures in their safety management systems to protect ships from cyber-incidents.
Specifically, a new dedicated annex provides measures that all companies should consider implementing to address cyber risk management in an approved SMS.
According to the guidelines, a proper cyber risk management should:
- Identify the roles and responsibilities of users, key personnel, and management both ashore and on board
- Identify the systems, assets, data and capabilities, which if disrupted, could pose risks to the ship’s operations and safety
- Implement technical and procedural measures to protect against a cyber incident and ensure continuity of operations
- Implement activities to prepare for and respond to cyber incidents.
However, the report notes that this is not so easy, as criminals are getting more inventive as the time passes.
OT risks
A key expansion in the guidelines regards operational technology. Ships have more and more Operational technology (OT) which includes Information technology (IT) and which can be connected to the internet. However, the risks associated with OT are different from IT systems.
GET THE SAFETY4SEA IN YOUR INBOX!
But what are the differences between IT and OT systems. Generally, OT systems control the physical world and IT systems manage data. Traditionally OT and IT were different, but with the internet, OT and IT are coming closer. Disruption of the operation of OT systems may affect onboard personnel, cargo, damage to the marine environment, and impede the ship’s operation.
Namely, malfunctioning IT may lead to significant delay of a ship’s unloading or clearance, but with malfunctioning or inoperative OT there can be a real risk of harm to people, the ship or the marine environment.
On a ship, the job may be less focused on protecting data while protecting operational systems working in the real world has direct safety implications. If the ECDIS system or software controlling an engine are hit with malware, or if it breaks down due to lack of compatibility after an update of software, it can lead to dangerous situations
Dirk Fry, chair of BIMCO’s cyber security working group and Director of Columbia Ship Management Ltd, explains.
The guidelines also provide examples of actual incidents to present some real-world situations that shipowners and operators have faced.
On the upside, a Cyber Security Survey by BIMCO, Fairplay and ABS Advanced Solutions, the joint Industry Guidelines on Cyber Security Onboard Ships, indicated that the industry is more aware of the issue and has increased cyber risk management training. Nevertheless, improvements have to made.
Supply chain dangers
Another focus area is the risk of malware infecting the ship’s systems through the many parties associated with the operation of a ship and its systems.
Guides include evaluating the security of service providers, providing a minimum set of requirements to manage supply chain or third-party risks and ensuring that agreements on cyber risks are formal and written.
The guidelines also emphasize the need for ships to be able to disconnect quickly and effectively from shore-based networks, where required.
Protection and detection measures
As BIMCO notes, it is important to protect critical systems and data with multiple layers of protection measures, which take into account the role of personnel, procedures and technology.
In order to establish a decent protective wall, connected OT systems on board should require more than one technical and/or procedural protection measure. Perimeter defences, such as firewalls, are also vital for preventing unwelcomed entry into the systems, but this may not be enough. A combined defence is needed, which consists of the following:
- Physical security of the ship in accordance with the ship security plan (SSP);
- Protection of networks, including effective segmentation;
- Intrusion detection;
- Periodic vulnerability scanning and testing;
- Software whitelisting;
- Access and user controls;
- Appropriate procedures regarding the use of removable media and password policies;
- Personnel’s awareness of the risk and familiarity with appropriate procedures.
The following infographic presents ideal ways to carry out a decent cyber risk management approach:
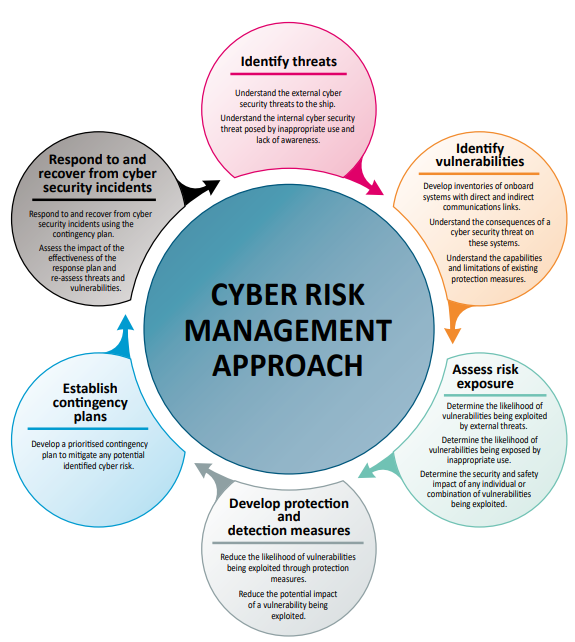
Credit: BIMCO
For further advice on how to prevent cyber attacks, click the PDF herebelow



















